Next: Virtual Hosting Services Up: Hosting Services Previous: Generalized status API Contents
The Hosting API is designed to be low level enough that middleware systems can be built on top of it, and high level enough to be useful for applications without supporting middleware.
|
|
|
|
|
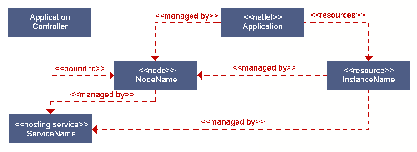
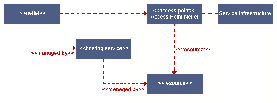
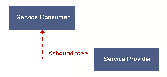
Figures ![[*]](crossref.png) through
through ![[*]](crossref.png) show the various
ways we depict relationships between hosting services, netlets, and
resources.
show the various
ways we depict relationships between hosting services, netlets, and
resources.
As an illustration, consider a simple pattern for Jtrix services. Applications following this pattern have the following characteristics:
The Helper service deals with boilerplate details like service advertisement, user interface, codebase download, and master election. It may be an entirely separate service, or be created to run only this application.
There may be different types of worker. Each worker type may be associated with resource instances. When a worker fails, it should be replaced with a worker connected to the same resources, if possible.
Only workers of a particular type are eligibile to be master. The other workers of that type are designated as backup masters
All changes to application state occur on the master and are propagated from the master to the backups. In the event of master failure, a new master is elected from the available backups. The most up to date backup is preferred.
Some operations must be performed by the master. These operations require access to up to date state information, for state integrity purposes. These operations are routed from backup controllers to the master over worker-to-worker RPC. Other operations may be performed using the (possibly out of date) backup copy of the state available on any worker. These decisions are application specific.
Access point netlets use RPC to communicate with a worker. The criteria for selecting the worker are as above.
The lifecycle of such an application will involve the following steps:
KEN must first obtain a Warrant for a hosting service. This involves some kind of contract negotiation, which may be explicit or implicit, inside or outside of Jtrix. The Warrant itself is merely an XML document. Some possibilities are:
He uses a web interface to agree to the contract, make payment provision, and download the warrant. Payment may have to be made when the service is used, via a Wallet service, or the wallet may have to be provided to the web site. Maybe just a credit card is required.
KEN now initialises his application. This involves the creation of a Bootstrap Descriptor which describes the application's bootstrap netlet, which is a special netlet written to start the application. Applications will be distributed with a mechanism to create this initial descriptor. This mechanism may require arguments to configure the application, or may be a complicated GUI style app. The bootstrap netlet will need, as a minimum, the warrant for the hosting service.
KEN uses a launcher application to start the application. The launcher application starts the bootstrap netlet, using the Bootstrap Descriptor. A complicated application may include its own launcher as part of the installation mechanism, bypassing the use of an explicit Bootstrap Descriptor.
The launcher application stays around long enough to ensure that the bootstrap has completed successfully, or to report the reason for failure. It can do this by interacting directly with the bootstrap netlet.
The bootstrap netlet uses the hosting warrant to create the first worker netlet. It can use the hosting services status reporting mechanism to retrieve initialisation dependent objects from the worker netlet, or the reason for startup failure.
In order to bind the hosting service warrant, the launcher application needs to provide a node environment. A convenient way of doing this is to embed nodality in the laucher.
Once the bootstrap netlet is started, it must initialise the application, and provide any required feedback to KEN.
Helper services used by the application may need to be initialised. If a helper service is used to serve the application codebase, then the bootstrap should upload the codebase at this point. The filenames for the codebase and the warrant for the helper service (and any other configuration parameters necessary to the application) are supplied during the creation of the bootstrap descriptor. The interaction mechanism used to control the bootstrap process may be used to read or write files during the bootstrap process.
A helper service may also be used to handle binding requests, and that service may also be initialised at this point. It may be necessary to initialise hosting resources or helper services in order to generate an initial warrant for the applications own service, for instance, to find binding protocol addresses if these are not known in advance.
If the helper service is to run on the same hosting service, then it should be bootstrapped separately, before the application is bootstrapped.
Application initialisation consists of using the hosting service to run the first application worker, which will become the master worker. Resources may need to be instantiated, connected and mapped for the controller use. Helper services may also be mapped as resources, if required.
Once the worker has initialised, any required feedback may be picked out of the controllers status via the hosting service, and reported back to KEN. Similarly, any failure feedback can be reported back.
Once the controller has sucessfully started, the bootstrap netlet can exit,and the launcher program can terminate.
If the application provides a Jtrix service, it must advertise that service. This may be done internally, or more likely, via a helper service. The helper service will likely need configuring to properly service the bind requests for this application.
The first controller should arrange for at least one backup if the application is to be fault tolerant. RPC links must be established to backups, and initial state propagated if necessary.
The hosting services also allow for an auto bootstrap mechanism if a control lease expires. This lease may have only one active lessor, and this mechanism may be used in a master election process if necessary. The autobootstrap mechanism may be used to reconnect ``orphaned'' parts of an application by binding an external service. If this mechanism is to be used, it should be initialised, and the lease periodically renewed.
If the application provides an external service, then the listener should also be established at this point.
Any necessary information about the deployment of the service may be fed back to KEN via the Hosting services status reporting mechanisms.
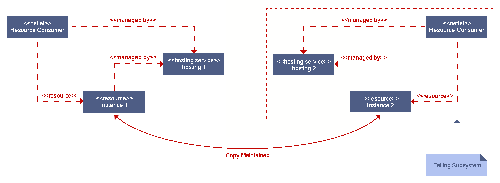
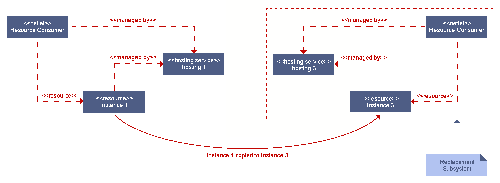
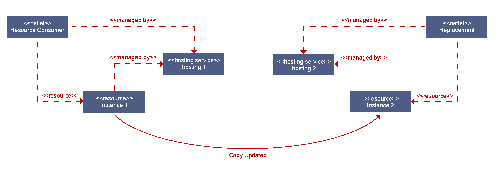
If a backup controller fails, due to netlet or node malfunction, it
should be replaced. Ideally, it should be replaced with a new netlet
bound to the same resources. If this is not possible, the state must
be reinitialised from another backup or the master. This is shown
in figure ![[*]](crossref.png) .
.
|
Reuse of the resource might be worthwhile for a number of reasons, including the preservation of an IP address, or to avoid copying a large amount of data.
If the master node fails, a new master should be elected from the remaining backups. The new master controller should follow a startup sequence similar to that detailed for the first master controller.
Service binding will result in the creation of access point netlets. These netlets will make network requests which must be serviced.
The master and backups may have to service external network requests.
At some point, the application will need to be terminated. The master should arrange for all netlets to terminate.
The hosting warrant can be used to reconnect to the hosting service if desired, for manual status inspection or forced termination. Standard user interfaces can be used for this, much as a traditional operating system provides standard interfaces for process inspection or termination.
![[*]](crossref.png) ) which handles
much of the boilerplate involved in such an application.
) which handles
much of the boilerplate involved in such an application.
Other patterns and corresponding frameworks are of course possible.
Jim Chapman 2001-08-16